The Kerberos security can be used in Stambia through a dedicated Metadata offering the possibility to define all the necessary information.
This article details how to create and configure it, and what are the available properties.
Prerequisites:
- Stambia DI Designer S18.3.6 or higher
This Metadata is only supported in Hadoop technologies for the moment.
Metadata
The Kerberos Metadata allows to define global server properties and a list of Principal nodes representing Kerberos accounts.
Below is an example of a Kerberos Metadata containing the Principals for some services on an Hadoop secured cluster:
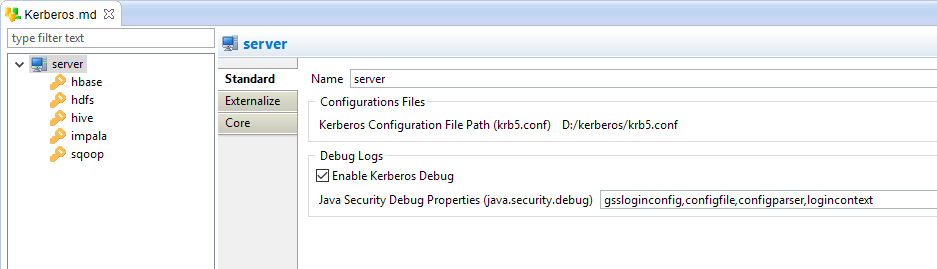
Server node
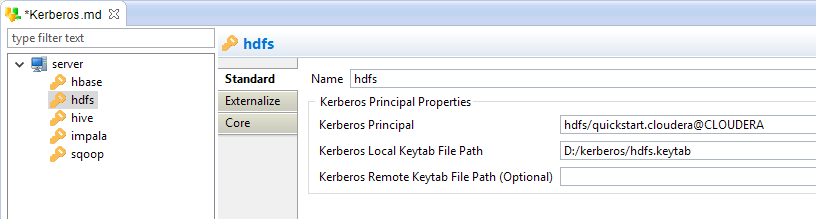
Principal node
Metadata creation
Create first the Kerberos Metadata, as usual, by selecting the technology in the Metadata Creation Wizard:
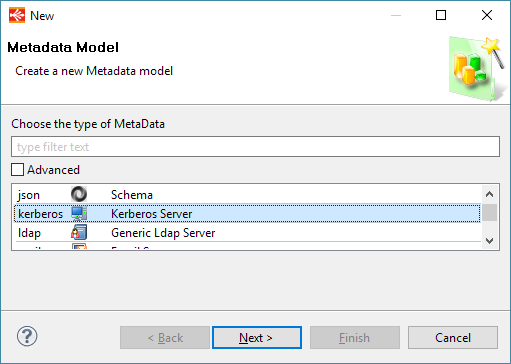
Click next, choose a name and click on finish.
Configuration of the server properties
You can now start configuring the server properties, which represent the global Kerberos properties shared with all the Principals.

The following properties are available:
| Property | Mandatory | Description | Example |
| Kerberos Configuration File Path | Yes |
Path to the Kerberos configuration file. This is a file usually named krb5.conf and which contains the location of the Kerberos server and necessary information to perform the Kerberos connection. Note that this is a system property that is global and unique on the Java Virtual Machine. You can only use one Configuration file at a time and changing it requires to restart the Designer / Runtime. |
D:/kerberos/krb5.conf |
| Enable Kerberos Debug | No |
Optional debug property that allows to print more information in the Runtime and Designer console when performing Kerberos connections. This can help to debug connection issues, as Kerberos will return more details and logs about the connection operations. To launch the Designer console, start the Designer with stambia.exe -console |
|
| Java Security Debug Properties | No |
Optional comma separated list of debug values that should be returned by Java. This specifies the java.security.debug Java property, which defines the debug logs that should be returned. When you are debugging Kerberos connection issues, we advise to set it to the example value to get precise log information. |
gssloginconfig,configfile,configparser,logincontext |
Configuration of the Principals
In Kerberos, an account in called a 'Principal'.
In the Kerberos Metadata, you can add as many principals as required, representing your different services, organizations, ...
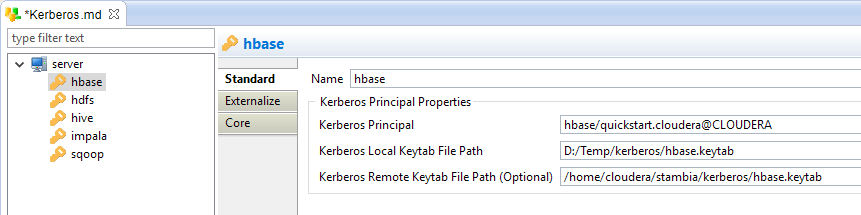
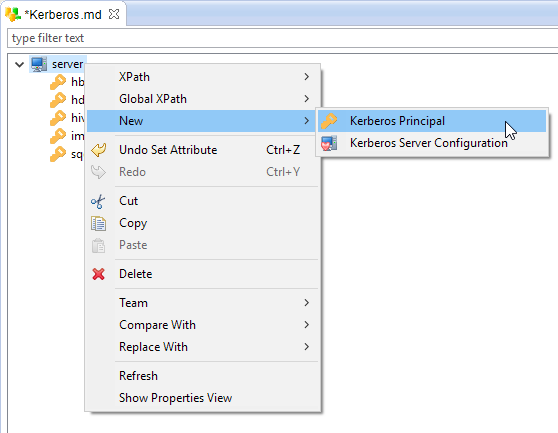
To add a new Principal, right click on the server node and choose new > Kerberos Principal:
The following properties are available:
| Property | Mandatory | Description | Example |
| Name | Yes |
Logical label (alias) to identify the Principal. |
hbase |
| Kerberos Principal | Yes |
Kerberos Principal name. The Kerberos Principal must meet the standard Kerberos Principal syntax, which is as follow: primary/instance@REALM |
hbase/quickstart.cloudera@CLOUDERA |
| Kerberos Local Keytab File Path | Yes |
Local Path to the Keytab file associated to the Principal. It must be reachable by the Designer / Runtime. |
D:/kerberos/hbase.keytab |
| Kerberos Remote Keytab File Path | No |
Optional remote Path to the Keytab file associated to the Principal. Templates and tools that are launching commands over SSH on servers secured with Kerberos requires to perform a Kerberos connection on the server, before operating. This property specifies the path of the Keytab on the remote server. |
/home/cloudera/stambia/kerberos/hbase.keytab |


